Information Security MIE 114
Objectives
- Upon completion of this course, participants will have gained knowledge of information security concepts, basic components and applications.
- to make students aware with basic fundamentals of information security,
- to know the various codes and attacks,
- to know the detailed principles of cryptography and other security techniques
Unit 1: Introduction to Information Security (4 Hrs)
The History of Information Security, What Is Information Security, Critical Characteristics of Information, Information Security Concepts and Practices (CIA Triad & Other Models), Balancing Security and Access
In-depth Explanation
The field of information security (often abbreviated as InfoSec) has evolved dramatically since its origins in the mid-20th century. It began with military cryptography during World War II (notably the German Enigma machine and Allied code-breaking efforts at Bletchley Park) and formalized in the 1970s–1980s with the rise of computer networks and early standards like the U.S. Department of Defense's Orange Book (TCSEC – Trusted Computer System Evaluation Criteria) in 1983.
By January 2026, InfoSec has transformed into a comprehensive discipline protecting digital ecosystems against sophisticated threats including AI-generated deepfakes, quantum computing attacks capable of breaking classical encryption, supply chain compromises in IoT/5G networks, and nation-state cyber operations. Modern InfoSec integrates zero-trust architectures, AI-driven behavioral analytics, and post-quantum cryptography to safeguard confidentiality, integrity, and availability in hyper-connected environments.
At its foundation lies the **CIA Triad** — the cornerstone model of information security:
- Confidentiality: Ensures information is accessible only to authorized individuals. Techniques include strong encryption, access controls, and zero-knowledge proofs. In 2026, this extends to defending against AI-powered surveillance and inference attacks on anonymized data.
- Integrity: Protects data from unauthorized modification or destruction. Achieved through cryptographic hashing, digital signatures, version control, and blockchain for immutable audit trails. Advanced defenses now use AI anomaly detection to spot subtle manipulations.
- Availability: Guarantees timely and reliable access to information and systems. Implemented via redundancy, DDoS protection, backups, and high-availability architectures. Contemporary challenges include resilience against large-scale ransomware-as-a-service (RaaS) and cloud provider outages.
Critical Characteristics of Information — Accuracy, Timeliness, Relevance, and Completeness — remain essential in the age of big data, generative AI, and misinformation campaigns. These qualities ensure information remains trustworthy and useful for decision-making.
Security vs. Access represents a perpetual balancing act: excessive security can impede legitimate business operations and innovation (e.g., blocking federated learning in collaborative AI projects), while insufficient security exposes organizations to catastrophic breaches. Modern approaches like **least privilege**, **zero trust** ("never trust, always verify"), and **privacy-by-design** (aligned with updated GDPR and emerging AI regulations) help strike this balance effectively.
Visual Representations
Explore these high-resolution diagrams illustrating the CIA Triad, its historical evolution, and modern security-access balance:
 |
Source: Medium – Understanding the CIA Triad (Educational Use Only)
other Similar Infographic Link for more knowledge.
Source: Cybersecurity Writeups – CIA Triad Pillars
Source: GeeksforGeeks – The CIA Triad in Cryptography
Source: UniNets – What is CIA Triad?
Source: Fortinet – CIA Triad Overview
Source: Facebook Cybersecurity Group – Three Principles of InfoSec
Recommended Video Resource
Professor Messer – The CIA Triad (CompTIA Security+ SY0-701 – Excellent foundational explanation)
Critical Thinking Exercises
In May 2021, the DarkSide ransomware group compromised Colonial Pipeline via a weak VPN credential, encrypting systems and demanding $4.4 million in Bitcoin. The company shut down operations for days, causing widespread fuel shortages and panic buying along the U.S. East Coast.
This incident severely impacted Availability (pipeline offline) and Integrity (data encrypted/untrustworthy), while highlighting poor Confidentiality controls. By 2026, similar attacks increasingly use AI-optimized phishing and supply-chain vectors, underscoring the need for MFA, zero-trust, and AI-driven threat hunting.
What if a commercially viable, cryptographically relevant quantum computer emerges by late 2027, breaking RSA and ECC encryption widely used today? How should organizations urgently transition to post-quantum cryptography (e.g., NIST PQC standards like CRYSTALS-Kyber) while maintaining the CIA Triad, managing massive costs, retrofitting legacy systems, and avoiding service disruptions in global finance, healthcare, and critical infrastructure?
Unit 2: Malicious code and application attacks (8 Hrs)
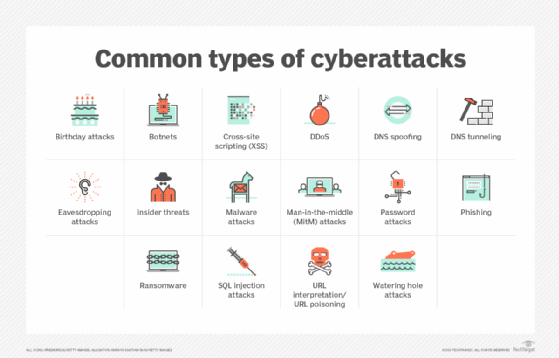
Types of Attacks: Malicious Code (Viruses, Worms, Trojans, Ransomware), Password Attacks, DoS/DDoS, Web Application Attacks (SQL Injection, XSS, CSRF), Reconnaissance Attacks, Masquerading Attacks, Modern AI-Enhanced Threat Landscape
In-depth Explanation
Attacks in information security are deliberate attempts to exploit vulnerabilities, directly targeting the CIA Triad (Confidentiality, Integrity, Availability). In January 2026, attackers increasingly leverage artificial intelligence, automation, and massive breached data ecosystems to make attacks faster, stealthier, and more adaptive than ever.
Malicious code remains the most common entry point:
- Viruses attach to legitimate files and require user action to spread.
- Worms self-replicate across networks without interaction (e.g., via unpatched vulnerabilities).
- Trojans disguise as useful software to deliver payloads like backdoors.
- Ransomware encrypts data and demands payment — 2026 variants use AI for polymorphic code that mutates to evade signature-based detection (e.g., GANs generating undetectable variants).
Password attacks include brute-force (trying all combinations), dictionary attacks, rainbow tables (precomputed hashes), and now AI-powered credential stuffing using billions of leaked credentials from dark web markets.
DoS/DDoS overwhelms systems to deny availability; modern attacks use AI-orchestrated botnets of compromised IoT devices (millions of cameras/routers) for volumetric floods reaching terabits per second.
Web application attacks exploit code flaws: SQL injection (manipulating database queries), XSS (injecting malicious scripts into pages), CSRF (tricking users into unwanted actions). In 2026, serverless (AWS Lambda, Azure Functions) introduces new risks like event-data injection and function chaining exploits.
Reconnaissance gathers intelligence via port scanning, OS fingerprinting, and social engineering — now supercharged by AI data mining from public sources (LinkedIn, GitHub, social media via NLP).
Masquerading involves impersonation: Man-in-the-Middle (MitM), IP/email spoofing, and increasingly realistic deepfake audio/video for executive fraud (CEO voice cloning in vishing attacks).
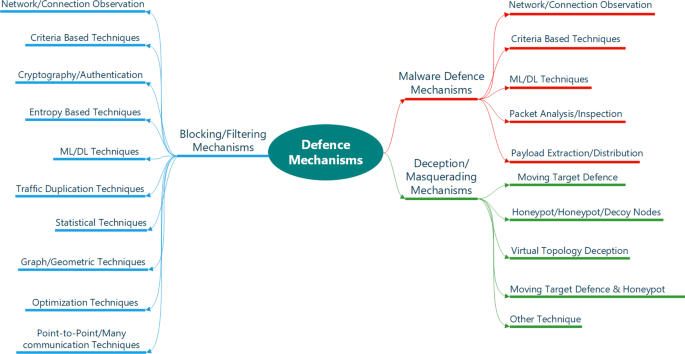
2026 Advanced Considerations: Fully autonomous AI attack chains (recon → exploit → lateral movement → exfiltration) using reinforcement learning. Defenses must shift to proactive behavioral analytics, deception tech (honeypots), and ML-based anomaly detection.
Visual Representations
High-resolution diagrams and flowcharts showing attack classification, progression, CIA impacts, and 2026 countermeasures:
Source: TechTarget – Common Types of Cyber Attacks
 |
Source: ScienceDirect – DoS Attack Overview Diagram |
 |
| Source: SAGE Journals – ML in Cybersecurity Attack Survey |
 |
Source: ScienceDirect – Ethical Hacking IoT Attack Vectors
 |
https://media.springernature.com/lw685/springer-static/image/art%3A10.1007%2Fs10207-023-00764-1/MediaObjects/10207_2023_764_Fig7_HTML.png
Source: Springer – SDN Defense Mechanisms Diagram
Recommended Video Resource
Professor Messer – Malware Overview & Types (CompTIA Security+ SY0-701 – Covers viruses, worms, ransomware & more)
Critical Thinking Exercises
Attackers (suspected nation-state) compromised SolarWinds Orion software updates, injecting a backdoor (SUNBURST) that masqueraded as legitimate code. This affected ~18,000 organizations, including U.S. government agencies, allowing persistent access and data exfiltration for months.
By 2026, AI-enhanced supply chain attacks automate vulnerability discovery and code injection, making zero-trust software validation, SBOMs (Software Bill of Materials), and continuous monitoring essential defenses.
What if an autonomous AI agent, trained on massive breach datasets, performs real-time reconnaissance by scraping LinkedIn profiles, company GitHub repos, and social media to craft hyper-personalized spear-phishing campaigns with deepfake video attachments? How should detection evolve — behavioral biometrics, AI red-teaming, or mandatory deepfake detection standards — to counter such adaptive, low-and-slow threats without crippling usability?
Unit 3: Cryptography and Key Management (8 Hrs)
Symmetric & Asymmetric Cryptography, DES, AES, RSA, ECC, Hash Functions, Digital Signatures, PKI, Key Management, Post-Quantum Cryptography (PQC)
In-depth Explanation
Cryptography is the mathematical science of securing data against unauthorized access, modification, or forgery. It underpins confidentiality, integrity, authentication, and non-repudiation in modern systems.
Symmetric ciphers use a single shared key:
- DES (56-bit key) — now obsolete due to brute-force vulnerability (cracked in hours in 1998).
- AES (128/192/256-bit keys) — current gold standard, quantum-resistant against known attacks (Grover's algorithm only halves effective key strength).
Asymmetric (public-key) systems use key pairs:
- RSA — based on prime factorization difficulty (2048–4096 bits recommended).
- Elliptic Curve Cryptography (ECC) — same security with much smaller keys (256-bit ≈ 3072-bit RSA), ideal for mobile/IoT.
Hash functions (e.g., SHA-3 family) create fixed-size digests for integrity — must be collision-resistant, preimage-resistant, and second preimage-resistant.
Digital signatures combine hashing + asymmetric encryption (signer uses private key) for authenticity and non-repudiation.
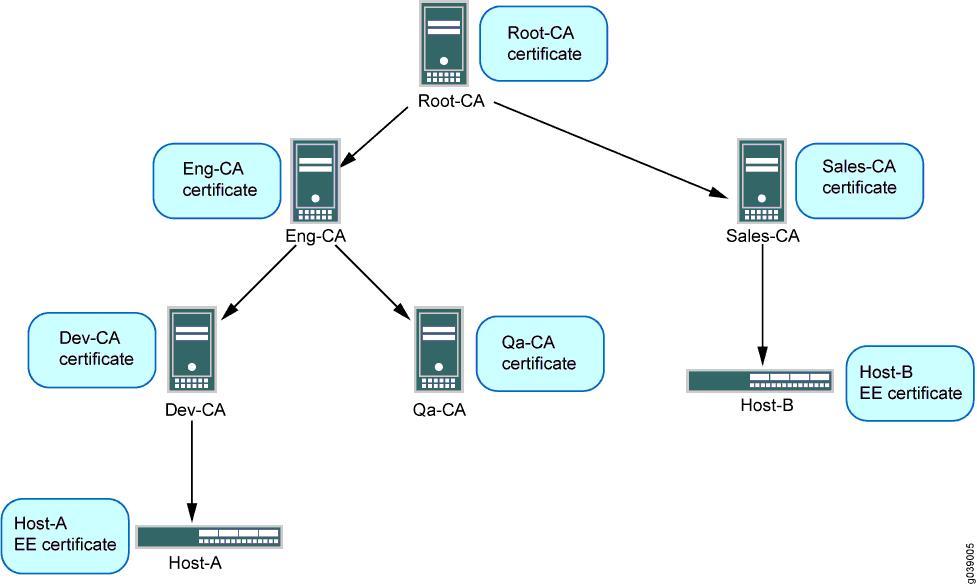
PKI (Public Key Infrastructure) builds trust chains: Root CA → Intermediate CAs → End-entity certificates, with CRL/OCSP for revocation.
2026 Nuances: Quantum computing threatens RSA/ECC via Shor's algorithm. NIST has standardized Post-Quantum Cryptography (PQC): CRYSTALS-Kyber (key encapsulation), CRYSTALS-Dilithium (signatures), SPHINCS+, FALCON. Hybrid schemes (classical + PQC) are now standard. AI accelerates cryptanalysis but also helps design quantum-resistant algorithms.
Visual Representations
Layered PKI architecture diagrams, certificate flows, symmetric/asymmetric comparison, and PQC integration:
 |
Source: Medium – What is PKI? Microsoft Cloud PKI
 |
Source: Keyfactor – PKI CA Hierarchy
Source: Keyfactor – PKI Hierarchies & Root CAs
Source: Juniper – Certificate Chain Configuration Example
Recommended Video Resource
MIT OpenCourseWare – Cryptography & Authentication (Advanced concepts including public-key systems)
Critical Thinking Exercises
WannaCry exploited the EternalBlue SMBv1 vulnerability in unpatched Windows systems, spreading worm-like across networks. It used RSA-2048 for key exchange and AES-128 for file encryption, demanding Bitcoin ransoms. Impact: 200,000+ computers in 150 countries, including hospitals and factories.
In 2026, proactive PQC migrations and automatic patching prevent similar quantum-vulnerable exploits in global critical infrastructure (healthcare, energy).
What if a major global Certificate Authority (CA) is compromised by an AI-orchestrated attack (e.g., exploiting insider access + deepfake social engineering), invalidating millions of trusted certificates overnight? How would PKI ecosystems execute rapid, coordinated transitions to post-quantum algorithms (Kyber/Dilithium hybrids) while preventing widespread e-commerce, banking, and VPN disruptions — considering legacy system compatibility and global certificate re-issuance logistics?
Unit 4: Access Control (5 Hrs)
Identification, Authentication, Authorization Techniques; Models (DAC, MAC, RBAC, ABAC); Least Privilege, Zero-Trust, AI & Blockchain Integration
In-depth Explanation
Access Control is the selective restriction of access to resources, ensuring only authorized entities can perform allowed actions while protecting the CIA Triad. It consists of three core processes:
- Identification: Claiming an identity (username, email, employee ID, or biometric template).
- Authentication: Proving the claimed identity. Classic factors:
- Something you know (password/PIN)
- Something you have (smart card/token/app)
- Something you are (fingerprint, iris, facial recognition)
- Something you do (keystroke dynamics, gait analysis)
- Authorization: Determining what the authenticated user is allowed to do. Key models include:
- DAC (Discretionary Access Control): Owner decides permissions (e.g., file sharing in Windows)
- MAC (Mandatory Access Control): System-enforced based on labels (military/government, e.g., SELinux)
- RBAC (Role-Based Access Control): Permissions tied to roles (e.g., "HR Admin" vs. "Employee") – most common in enterprises
- ABAC (Attribute-Based Access Control): Dynamic, policy-driven using attributes (user role, time, location, device health) – ideal for cloud/zero-trust
Methodologies emphasize least privilege (give only needed access), need-to-know, and zero-trust architecture (assume breach — verify every request continuously).
2026 Advanced Nuances: AI-powered anomaly detection flags unusual access (e.g., login from new country at odd hours). Blockchain enables **self-sovereign identity** (SSI) — users control their credentials via decentralized identifiers (DIDs), reducing reliance on central authorities and enhancing privacy.
Visual Representations
Multiple diagrams showing access control models, workflows, zero-trust, and AI integration:
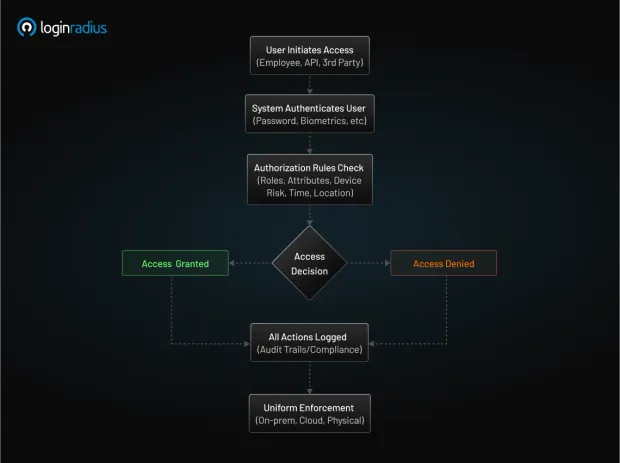
Source: LoginRadius – Access Control Flowchart (Educational Use Only)

Source: ResearchGate – RBAC Workflow (Educational Use Only)
Recommended Video Resource
Professor Messer – Authentication Factors & Models (CompTIA Security+ SY0-701)
Critical Thinking Exercises
Attackers used phone spear-phishing to trick Twitter employees into giving admin access, then hijacked high-profile accounts (Elon Musk, Barack Obama) for Bitcoin scam. Weak social engineering bypassed multi-layer controls.
By 2026, **AI-behavioral authentication** and **privileged access management (PAM)** with just-in-time elevation could detect anomalous admin logins and prevent such incidents.
What if AI deepfakes evolve to perfectly mimic biometrics (voice + face + behavior) in real-time, fooling facial recognition and voice auth systems? How should organizations transition to hybrid/multi-modal authentication (e.g., combining biometrics with hardware tokens + continuous ML monitoring + quantum-safe challenges) while maintaining usability and preventing lockouts?
Unit 5: Network Security (5 Hrs)
LAN & Wireless Security, Internet Threats, Countermeasures (Firewalls, IDS/IPS, VPNs), Zero-Trust Network Access (ZTNA), 5G/6G & Edge Risks
In-depth Explanation
Network Security protects data during transmission and ensures the integrity/availability of interconnected systems in LAN, WAN, and cloud environments.
LAN Security uses segmentation (VLANs to isolate departments), firewalls (stateful inspection), and NAC (Network Access Control) to authenticate devices before granting access.
Wireless Security has evolved: WPA3 (with Simultaneous Authentication of Equals – SAE) replaces WPA2, protecting against offline dictionary attacks. Challenges persist in IoT mesh networks with weak default credentials and legacy protocols.
Internet Threats include phishing, malware distribution, zero-day exploits, and advanced persistent threats (APTs). Countermeasures:
- IDS/IPS for signature & anomaly detection
- VPNs (IPsec or WireGuard) for encrypted tunnels
- SD-WAN for intelligent routing & security overlays
2026 Advanced Nuances: AI-driven threats automate worm propagation and lateral movement. Defenses include ML-based Network Behavioral Analysis (NBA) and quantum-safe VPNs (PQC algorithms). 5G/6G introduces edge computing risks (distributed processing closer to devices) — mitigated by ZTNA (Zero-Trust Network Access), which verifies every connection regardless of location.
Visual Representations
Secure network topologies, wireless setups, threat flows, and ZTNA diagrams:

Source: TechSecretsHub – Firewall Network Architecture 2025 (Educational Use Only)
Recommended Video Resource
Professor Messer – Wireless Security Protocols (WPA3, SAE & More)
Critical Thinking Exercises
Exploited EternalBlue SMB vulnerability in unpatched Windows networks, spreading rapidly as a worm. Caused billions in damages (Maersk, Merck, FedEx). Poor network segmentation and patching enabled global propagation.
In 2026, **AI-automated patch management** and **micro-segmentation** (via ZTNA) prevent similar supply-chain disruptions.
What if cryptographically relevant quantum computers enable real-time decryption of current VPN traffic (breaking IPsec RSA/ECC)? How should enterprises migrate to post-quantum protocols (e.g., hybrid Kyber + AES) without downtime, ensuring compatibility with legacy devices and global supply chains?
Unit 6: Auditing and Monitoring (4 Hrs)
Penetration Testing Phases, Monitoring & SIEM, Incident Response, Threat Countermeasures, AI-Enhanced Auditing
In-depth Explanation
Auditing and Monitoring form the detective and responsive layers of information security, providing visibility into system activities, detecting anomalies, and enabling incident response to minimize damage and ensure compliance.
Penetration Testing (Ethical Hacking) simulates real attacks to identify vulnerabilities before malicious actors do. Standard phases (2026 standards):
- Planning & Reconnaissance: Scope definition, passive/active intel gathering (OSINT, AI-enhanced scraping)
- Scanning: Port/vulnerability scanning (Nmap, Nessus), AI-fuzzing for zero-days
- Gaining Access: Exploitation (Metasploit, custom exploits)
- Maintaining Access: Backdoors, persistence mechanisms
- Analysis & Reporting: Findings, risk rating, remediation recommendations
Monitoring uses **SIEM** (Security Information and Event Management) to collect, correlate, and analyze logs in real-time. Modern SIEM integrates AI/ML for anomaly detection (e.g., UEBA – User and Entity Behavior Analytics) and predictive threat hunting.
Incident Response follows frameworks like NIST: Preparation → Identification → Containment → Eradication → Recovery → Lessons Learned.
2026 Advanced Nuances: AI automates pentesting (autonomous red-team agents) and SIEM threat forecasting. Quantum-safe logging and blockchain for tamper-proof audit trails are emerging standards.
Visual Representations
Penetration testing lifecycle diagrams, SIEM architecture with AI components:
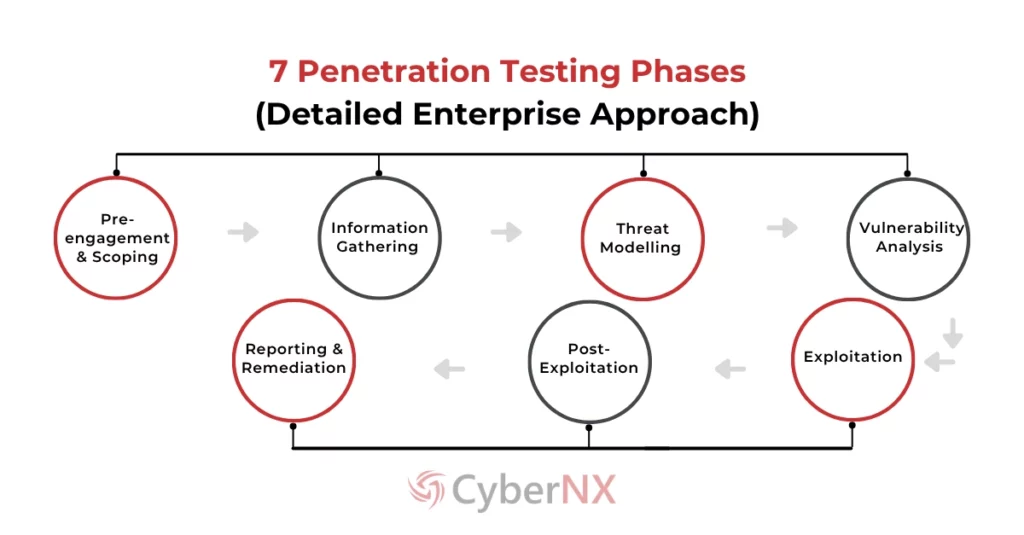
Source: CyberNX – 7 Penetration Testing Phases (Educational Use Only)

Source: ResearchGate – Penetration Testing Phases (Educational Use Only)
Source: ResearchGate – SIEM Components (Educational Use Only)
Recommended Video Resource
Professor Messer – Penetration Testing Concepts & Phases
Critical Thinking Exercises
Attackers exploited an unpatched Apache Struts vulnerability; poor monitoring allowed 147 million records to be exfiltrated undetected for months. Lack of SIEM correlation and pentesting failed to catch the entry point.
In 2026, AI-SIEM with predictive analytics flags anomalous database queries instantly, and automated pentesting tools prevent similar oversights.
What if AI fully automates penetration testing to generate self-evolving exploits faster than humans can patch? How should ethical guidelines, regulations (e.g., AI red-team mandates), and defensive AI evolve to regulate such tools while preventing weaponization?
Unit 7: Legal, Ethical and Professional issues in Information Security (6 Hrs)
Privacy Laws (GDPR, CCPA), IP & Licensing, International Standards (ISO 27001, NIST), Professional Ethics, AI Ethics in Security
In-depth Explanation
Legal and Ethical Aspects ensure responsible use of information security practices, balancing protection with rights, innovation, and accountability.
Privacy Laws: GDPR (EU) mandates data minimization, consent, and breach notification within 72 hours; CCPA/CPRA (California) gives consumers opt-out rights for data sales. 2026 updates incorporate AI processing transparency and high-risk AI impact assessments.
IP & Licensing: Copyrights protect software/code; patents cover algorithms (e.g., post-quantum crypto); open-source licensing (GPL, MIT) vs. proprietary. Violations lead to DMCA takedowns or lawsuits.
International Bodies & Standards: ISO 27001 (ISMS certification), NIST Cybersecurity Framework (voluntary US), ENISA (EU). These provide best practices for risk management.
Professional Ethics: (ISC)² Code of Ethics emphasizes integrity, confidentiality, competence. 2026 focus: AI bias in security tools (e.g., facial recognition false positives), responsible disclosure of vulnerabilities, and ethical hacking boundaries.
Visual Representations
Mind maps and compliance frameworks for legal/ethical aspects:

Source: Secureframe – NIST AI Risk Management Framework (Educational Use Only)
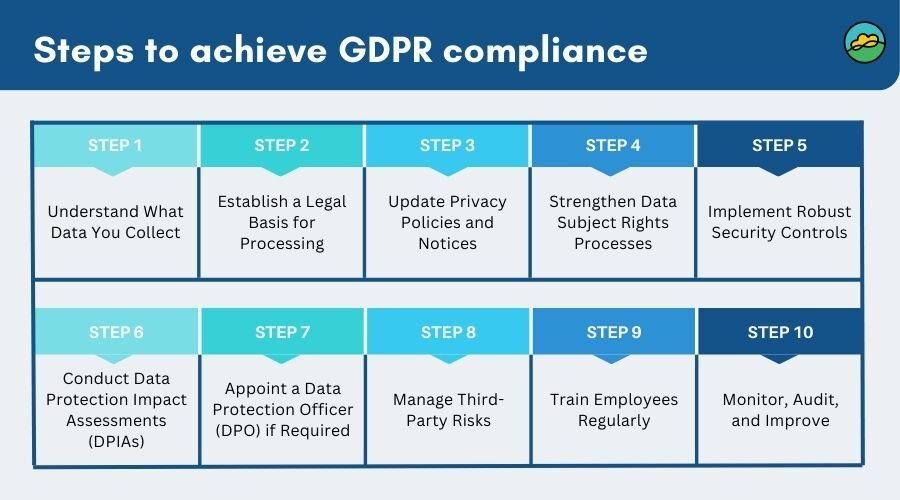
Source: TrustCloud – GDPR Compliance (Educational Use Only)
Recommended Video Resource
Professor Messer – Security Policies, Regulations & Ethics
Critical Thinking Exercises
Facebook data of 87 million users was harvested without consent for political profiling, violating privacy laws and ethics. Led to massive fines and GDPR enforcement acceleration.
In 2026, mandatory AI transparency and data sovereignty rules aim to prevent similar algorithmic misuse.
What if an ethical hacker discovers a critical zero-day in national infrastructure but faces legal threats for disclosure? How should international bodies harmonize coordinated vulnerability disclosure policies, safe harbor laws, and whistleblower protections in a world of AI-amplified threats?
Unit 8: Disaster Recovery and Business Continuity (5 Hrs)
BCP Lifecycle, Business Impact Analysis (BIA), RTO/RPO, DR Strategies, Backups & Failover, AI-Optimized Resilience
In-depth Explanation
Business Continuity Planning (BCP) ensures critical functions continue during/after disruptions; **Disaster Recovery (DR)** focuses on IT restoration.
BCP Lifecycle:
- Risk Assessment
- Business Impact Analysis (BIA) – identifies critical assets, RTO (Recovery Time Objective), RPO (Recovery Point Objective)
- Strategy Development
- Plan Implementation
- Testing & Maintenance
DR Strategies: Backups (full/incremental), failover sites (hot/cold/warm), cloud-native (AWS Backup, Azure Site Recovery). 2026 emphasizes quantum-resilient encryption for backups and AI predictive modeling for threat anticipation.
2026 Advanced Nuances: AI optimizes BIA (predicting impact via simulations) and automates failover. Edge computing and 5G require distributed DR plans.
Visual Representations
BCP lifecycle cycles and DR architecture diagrams:

Source: GeeksforGeeks – Business Continuity Plan (Educational Use Only)

Source: AWS – Disaster Recovery Architecture (Educational Use Only)
Recommended Video Resource
Professor Messer – BCP & DR Concepts
Critical Thinking Exercises
Devastated Puerto Rico's infrastructure; poor DR plans led to months-long outages in power, telecom, and healthcare. Lack of offsite backups and failover exacerbated recovery.
In 2026, AI-forecasted BCPs with cloud-native DR enable proactive resource allocation and faster recovery.
What if a massive solar flare causes a global electromagnetic pulse (EMP), wiping unshielded backups and data centers? How would DR plans evolve to include space-weather hardening, decentralized blockchain storage, and quantum-resilient off-world satellite backups while maintaining RTO/RPO for critical services?
Exam Questions & Solutions – Purbanchal University MSc IT (Information Security)
Model answers based on syllabus (2026 perspective). Click each question to expand the solution. Best for revision & scoring high!
Unit 1: Introduction to Information Security
1a: Define information security and explain the CIA Triad with real-world examples.
Information Security is the practice of protecting information from unauthorized access, use, disclosure, disruption, modification, or destruction.
CIA Triad:
• Confidentiality – Ensures data is accessible only to authorized persons (Example: Encryption in WhatsApp chats prevents eavesdropping).
• Integrity – Protects data from unauthorized changes (Example: Hashing in software downloads verifies no tampering).
• Availability – Guarantees timely access (Example: DDoS protection keeps banking websites online).
Video: CIA Triad – Professor Messer
1b: Discuss the balance between security and access in modern organizations (2026 context).
Security restricts access to protect assets (e.g., firewalls, MFA), while access enables productivity (e.g., remote work). Over-security hinders business (blocks innovation like federated learning), under-security causes breaches.
2026 balance: Zero-trust model (“never trust, always verify”) + privacy-by-design (GDPR AI updates) + least privilege principle.
Unit 2: Malicious Code and Application Attacks
2a: Differentiate between virus, worm, Trojan, and ransomware with examples.
• Virus: Attaches to files, needs user action (e.g., macro virus in Excel).
• Worm: Self-replicates over networks (e.g., WannaCry worm).
• Trojan: Disguises as useful software (e.g., fake antivirus with backdoor).
• Ransomware: Encrypts files, demands ransom (e.g., LockBit 2025–2026 variants).
Video: Types of Malware – Professor Messer
2b: Explain SQL Injection and XSS attacks with prevention methods.
• SQL Injection: Attacker injects malicious SQL via input fields to manipulate database (e.g., ' OR 1=1 -- ).
• XSS (Cross-Site Scripting): Injects malicious scripts into web pages viewed by users.
Prevention: Input validation, parameterized queries, output encoding, CSP (Content Security Policy).
Unit 3: Cryptography and Key Management
3a: Compare symmetric and asymmetric cryptography with examples of algorithms.
| Aspect | Symmetric | Asymmetric |
|---|---|---|
| Key | Single shared key | Public + Private key pair |
| Speed | Fast | Slower |
| Examples | AES-256 | RSA, ECC |
| Use | Bulk data encryption | Key exchange, digital signatures |
3b: What is Post-Quantum Cryptography? Name two NIST-standardized algorithms.
Post-Quantum Cryptography (PQC) designs algorithms resistant to quantum attacks (Shor's algorithm breaks RSA/ECC).
NIST 2024–2025 standards: CRYSTALS-Kyber (key encapsulation), CRYSTALS-Dilithium (digital signatures).
Unit 4: Access Control
4a: Explain the difference between authentication and authorization. List four authentication factors.
• Authentication: Verifies “who you are” (proves identity).
• Authorization: Determines “what you can do” after authentication.
Four factors: Something you know (password), have (token), are (biometric), do (behavioral).
4b: Compare RBAC and ABAC access control models.
| Aspect | RBAC | ABAC |
|---|---|---|
| Basis | Roles | Attributes (user, resource, environment) |
| Flexibility | Static | Dynamic |
| Use case | Enterprise (HR, Finance roles) | Cloud / Zero-Trust |
Unit 5: Network Security
5a: What is WPA3? How does it improve over WPA2?
WPA3 is the latest Wi-Fi security protocol (2018–2026 standard).
Improvements over WPA2: SAE (Simultaneous Authentication of Equals) resists offline dictionary attacks, 192-bit security mode, forward secrecy, better IoT protection.
5b: Explain Zero-Trust Network Access (ZTNA) and its importance in 2026.
ZTNA assumes no trust – verifies every user/device/request regardless of location.
Importance in 2026: Protects against remote work risks, AI-driven threats, and 5G/edge computing vulnerabilities.
Unit 6: Auditing and Monitoring
6a: List and briefly explain the five phases of penetration testing.
1. **Planning & Reconnaissance** – Define scope, gather intel.
2. **Scanning** – Identify vulnerabilities.
3. **Gaining Access** – Exploit weaknesses.
4. **Maintaining Access** – Establish persistence.
5. **Analysis & Reporting** – Document findings & recommend fixes.
Unit 7: Legal, Ethical and Professional Issues
7a: What are the key requirements of GDPR for organizations handling personal data?
• Lawful basis for processing
• Data minimization & purpose limitation
• Consent management
• Breach notification within 72 hours
• Data Protection Officer (DPO) for large-scale processing
Unit 8: Disaster Recovery and Business Continuity
8a: Define RTO and RPO. How are they used in Business Impact Analysis (BIA)?
• **RTO (Recovery Time Objective)**: Maximum acceptable downtime before recovery.
• **RPO (Recovery Point Objective)**: Maximum acceptable data loss (time between last backup and incident).
In BIA: Identify critical processes → set RTO/RPO → design DR strategies (backups, failover).
8b: Explain the difference between hot site, warm site, and cold site in disaster recovery.
• **Hot site**: Fully equipped, real-time mirrored data – immediate failover (expensive).
• **Warm site**: Partially equipped, data backed up periodically – hours to activate.
• **Cold site**: Basic facility only – days/weeks to set up (cheapest).